When it comes to protecting patient information in healthcare, two core elements of HIPAA (Health Insurance Portability and Accountability Act) often come up: HIPAA Privacy Rule and HIPAA Security Rule. While they are closely related, they serve different purposes. Understanding the differences between them is essential for compliance, avoiding fines, and ensuring the confidentiality of sensitive health data.
In this article, we’ll explain the key differences between HIPAA Privacy Policies and HIPAA Security Policies, their objectives, and why both are crucial for healthcare providers, insurers, and business associates.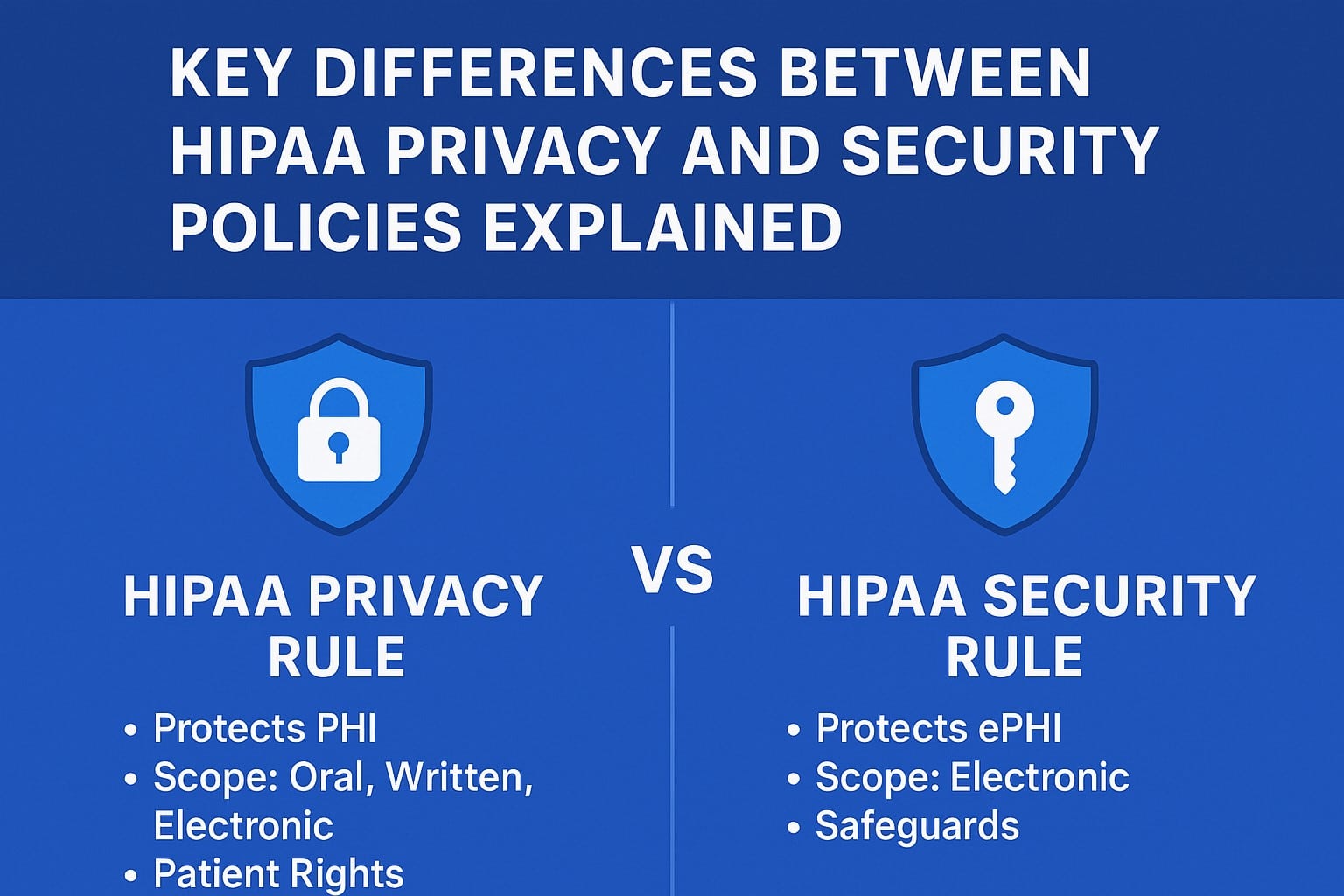
What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule sets national standards for safeguarding Protected Health Information (PHI). PHI refers to any identifiable health information about patients—such as medical records, lab results, billing information, or insurance details.
Key Points of the Privacy Rule:
-
Scope: Applies to all forms of PHI—oral, written, and electronic.
-
Objective: Protect patient rights by regulating how PHI is collected, used, and disclosed.
-
Patient Rights: Patients have the right to access, amend, and request restrictions on their health information.
-
Covered Entities: Healthcare providers, health plans, and business associates must comply.
Essentially, the Privacy Rule is about who can access patient information and under what circumstances.
What is the HIPAA Security Rule?
The HIPAA Security Rule focuses specifically on protecting Electronic Protected Health Information (ePHI). It ensures that healthcare organizations implement safeguards to keep digital patient records safe from breaches and unauthorized access.
Key Points of the Security Rule:
-
Scope: Applies only to electronic PHI (ePHI).
-
Objective: Ensure the confidentiality, integrity, and availability of digital health data.
-
Safeguards Required:
-
Administrative safeguards – policies, procedures, and workforce training.
-
Physical safeguards – securing servers, devices, and workstations.
-
Technical safeguards – encryption, access controls, audit logs, and authentication.
-
In short, the Security Rule is about how patient data is protected in electronic systems.
Key Differences Between HIPAA Privacy and Security Policies
| Aspect | HIPAA Privacy Rule | HIPAA Security Rule |
|---|---|---|
| Type of Data | Protects PHI in all forms (oral, written, electronic) | Protects only electronic PHI (ePHI) |
| Primary Focus | Patient rights and control over health information | Safeguarding systems that store and transmit ePHI |
| Implementation | Defines what information can be shared and with whom | Requires technical, administrative, and physical safeguards |
| Patient Involvement | Grants rights to patients regarding their data | No direct patient rights; focuses on data security measures |
| Enforcement | Ensures compliance in handling PHI | Ensures security of technology and digital systems |
Why Both Rules Are Important
Both the Privacy and Security Rules complement each other:
-
The Privacy Rule protects patient rights.
-
The Security Rule ensures technological safeguards keep digital PHI safe.
Together, they provide a comprehensive framework for healthcare data protection, helping organizations maintain compliance while fostering trust with patients.
Consequences of Non-Compliance
Failure to comply with HIPAA Privacy or Security Rules can result in:
-
Heavy fines (ranging from thousands to millions of dollars).
-
Legal action and penalties.
-
Loss of reputation and patient trust.
-
Increased risk of data breaches and cyberattacks.
Final Thoughts
The HIPAA Privacy and Security Rules may overlap, but they serve distinct purposes. The Privacy Rule focuses on who can access health information, while the Security Rule emphasizes how electronic data is protected.
For healthcare organizations, compliance with both policies is not optional—it’s essential for avoiding penalties, maintaining patient trust, and safeguarding sensitive health information.
By implementing strong HIPAA policies, conducting regular audits, and training employees, organizations can build a culture of compliance and data protection.
