A cyber incident can turn into a business crisis in hours—sometimes minutes. The difference between a contained incident and a full-scale breach often comes down to whether your organization has a clear, tested, and repeatable incident response plan that aligns IT, Security, Legal, HR, Communications, and Executive Leadership.
The Cyber Security Incident Response Plan Template Suite is a premium, enterprise-focused toolkit designed to help organizations build a board-ready, audit-friendly, and operationally usable incident response program. It includes 13 core templates and a library of 21 scenario-based response templates, each provided as a Completed Example (so teams see what “good” looks like) and a Client Fillable Template (so you can customize quickly), plus a one-page Coverage Checklist for quality assurance.
If you need to create (or upgrade) an enterprise Cybersecurity Incident Response Plan (CSIRP) without reinventing the wheel, this suite gives your team a structured path—from governance through execution and continuous improvement.
What Is a Cybersecurity Incident Response Plan?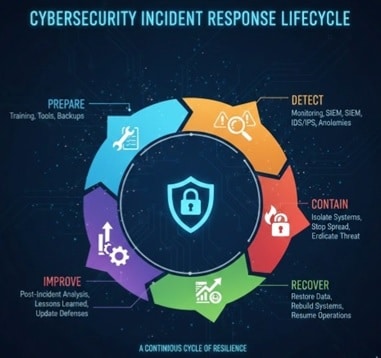
A Cybersecurity Incident Response Plan (CSIRP) is a documented, organization-wide playbook that defines how your company prepares for, detects, analyzes, contains, eradicates, recovers from, and learns from cybersecurity incidents. A strong CSIRP does more than list technical steps—it establishes decision-making authority, escalation thresholds, communications workflows, evidence handling expectations, and documentation standards.
In practical terms, a CSIRP answers the questions every organization faces during an incident: Who leads? Who approves? Who communicates? What gets shut down? What must be preserved? How do we restore safely? How do we document decisions? Without those answers written and rehearsed, response efforts often become fragmented, slow, and risky.
Why a Cybersecurity Incident Response Plan Is Needed?
Most organizations have security tools. Fewer organizations have a coordinated operating model that ensures those tools lead to timely action. A CSIRP is needed because incidents aren’t purely technical events—they are business events with legal, financial, customer, and reputational consequences.
A CSIRP helps organizations:
- Reduce downtime and operational disruption by clarifying priorities and recovery criteria.
- Avoid costly mistakes (e.g., deleting evidence, communicating prematurely, restoring from unverified backups).
- Coordinate non-technical stakeholders (Legal, HR, Communications, Finance, business unit owners) at the right time.
- Meet regulatory timelines for reporting and notification by having pre-built workflows and templates.
- Build executive confidence through defined escalation criteria, consistent reporting, and decision matrices.
Most importantly, a CSIRP transforms incident response from an ad-hoc scramble into a repeatable business capability.
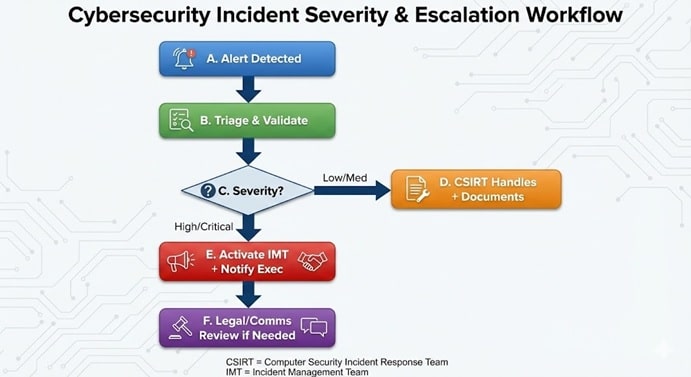
Which Regulations Require or Expect an Incident Response Plan?
Regulatory requirements vary by industry and geography, but many frameworks either explicitly require incident response plans/procedures or create obligations (notification, reporting, governance) that strongly necessitate having a formal plan.
Regulations and standards that explicitly require incident response planning or procedures
- NYDFS Cybersecurity Regulation (23 NYCRR Part 500) requires covered entities to establish a written incident response plan designed to respond to and recover from cybersecurity events.
- FTC Safeguards Rule (16 CFR Part 314) requires certain organizations to establish a written incident response plan, including roles, decision authority, communications, and documentation requirements.
- HIPAA Security Rule (45 CFR 164.308(a)(6)) requires covered entities/business associates to implement security incident procedures, including required response and reporting expectations.
- PCI DSS includes requirements for implementing an incident response plan (commonly referenced as Requirement 12.10 in PCI DSS guidance) for organizations handling payment card data.
- NERC CIP-008 (for entities in scope of North American bulk electric system reliability standards) requires documented Cyber Security Incident response plan(s) and implementation/testing expectations.
- EU DORA (Regulation (EU) 2022/2554) requires financial entities to define and implement an ICT-related incident management process to detect, manage, and notify incidents, including incident response procedures and communication plans.
- EU NIS2 (Directive (EU) 2022/2555) requires essential/important entities to implement cybersecurity risk-management measures that include incident handling and business continuity/crisis management, among other measures.
Regulations that drive incident-response readiness through notification/disclosure obligations
- GDPR (Regulation (EU) 2016/679) sets breach notification and documentation expectations, including the widely known 72-hour notification requirement in certain circumstances—organizations typically need a strong response plan to reliably meet these timelines.
- SEC cybersecurity disclosure rules require public companies to disclose cybersecurity incident information and describe cybersecurity risk management and governance processes—formal incident response processes help support consistent, defensible reporting.
Important note: This is general information, not legal advice. Requirements vary by jurisdiction, industry, and applicability—your counsel/compliance team should confirm what applies to your organization.
Benefits of Having a Cybersecurity Incident Response Plan
A CSIRP delivers value in both day-to-day operations and crisis moments:
- Faster, calmer response: Your team follows a practiced workflow instead of improvising under pressure.
- Clear executive decisions: Leaders get structured options and escalation triggers rather than vague technical updates.
- Reduced business impact: Better containment and recovery criteria reduce downtime and secondary damage.
- Better evidence and defensibility: Documented timelines, decision logs, and evidence handling reduce legal and insurance friction.
- Improved communications: Messaging is consistent and approved, reducing reputational risk and internal confusion.
- Continuous improvement: Post-incident actions are tracked and closed, strengthening the program over time.
How This Template Suite Helps You Build an Enterprise CSIRP
Many organizations “have a plan,” but it’s either too technical to be executable, too generic to be useful, or too fragmented to align stakeholders. The Cyber Security Incident Response Plan Template Suite is designed to solve that by providing:
- A management framework (CSIRMP) that governs the program, decision authority, stakeholder roles, and continuous improvement.
- A practical CSIRP that teams can actually use during a real event.
- A supporting procedure document that operationalizes consistent execution and documentation.
- A set of checklists, meeting templates, and tracking logs that provide structure during high stress.
- A library of 21 real-world scenario templates delivered with completed examples, so stakeholders can see the level of detail expected and replicate it quickly.
In short: this suite gives you the “what,” the “how,” and the “proof”—governance + operational steps + documentation artifacts.
What’s Included: 12 Core Templates and 63 Scenario Documents
This suite includes 75 documents out of which 12 are core templates and 63 are documents for scenarios. Scenarios are delivered as a 3-document package to support tabletop exercises, training, and repeatable incident response execution for 21 different scenarios. The three-document package includes for each scenario (a) Completed Example; (b) Client Fillable Template; (c) Coverage Checklist Appendix (1 page).
The following templates are included in the suite.
1) Step-by-step Guide for How to Use the Templates.
This guide is the “onboarding path” for the suite—helping teams understand how to sequence adoption, who should own each document, and how to customize efficiently. It also reduces implementation risk by showing how documents connect across governance, response execution, and post-incident improvement.
2) Cyber Security Incident Response Management Plan (CSIRMP)
The CSIRMP defines enterprise-wide governance: roles, authority, escalation, communications expectations, training/testing cadence, and program improvement. It keeps incident response aligned to business priorities and ensures stakeholders beyond IT (Legal, HR, Comms, Execs) are integrated.
3) Cyber Security Incident Response Plan (CSIRP)
The CSIRP is the operational plan teams follow during an incident, from detection through recovery and closure. It provides a consistent structure for incident phases, documentation, decision points, and coordination across teams.
4) Cyber Security Incident Response Management Procedure
This procedure translates policy/plan into repeatable execution—clarifying exactly how to run the incident process step-by-step. It strengthens consistency across responders and helps new team members follow the same cadence and documentation expectations.
5) Cyber Security Incident Response Plan Checklist
A response checklist reduces “missed steps” during stressful events—especially around containment decisions, evidence preservation, approvals, and communications. It’s ideal for war-room facilitation and for demonstrating procedural discipline to auditors.
6) Cyber Security Incident Response Preparation Checklist
Preparation checklists help validate that people, tools, access, contacts, secure comms, and documentation mechanisms are ready before an incident occurs. This template helps organizations identify gaps early—before response speed matters.
7) Cyber Security Vulnerability Response Checklist
This checklist supports vulnerability-to-incident workflow: intake, triage, severity scoring, patch/mitigation planning, validation, and communication. It helps ensure vulnerabilities are managed consistently, including escalations when exploitation is suspected.
8) CSIRT Meeting Agenda
A structured meeting agenda prevents war-room drift and ensures each session produces clear outputs: current status, decisions needed, actions assigned, and next milestones. It helps incident leaders keep stakeholders aligned without turning meetings into unproductive updates.
9) CSIRT Meeting Notes
Meeting notes capture decisions, risks, actions, and approvals in a format that can be shared, archived, and referenced later. This template strengthens defensibility and reduces confusion about “who approved what and when.”
10) Initial Internal Management Security Incident Alert
This template standardizes the first executive-facing alert, ensuring early communications include the right facts, unknowns, impact scope, immediate containment steps, and next decision points. It improves leadership confidence and reduces reactive escalation.
11) CSIRT Issues and Goals List
This document organizes the incident into a manageable set of problems to solve and goals to achieve, preventing teams from chasing noise. It’s especially useful when incidents expand in scope or when multiple workstreams operate in parallel.
12) CSIRT Action Tracking List
Action tracking is where response discipline becomes measurable: owners, due dates, dependencies, and completion status. This template makes follow-through visible and reduces the risk of incomplete containment or unsafe recovery.
13) CSIRT Member Activity Tracking Log
This log supports accountability and compliance by recording individual responder actions (what was done, when, and why). It also helps with after-action review and can support evidence trails when needed.
Scenario Templates and Completed Examples: 21 Real-World Incidents
Each scenario is designed to be used in two ways:
- Completed Example (shows the level of detail a “finished” document should contain), and
- Client Fillable Template (blank version for customization), plus a one-page Coverage Checklist to confirm nothing important was missed.
Scenario 1: Compromised Database Server
This scenario guides containment, credential resets, access logging, and integrity validation when a database host is suspected compromised. It also supports decision-making around service shutdown, customer impact, and forensic preservation.
Scenario 2: Worm Distributed Denial of Service (DDoS) Agent Infestation
Designed for bot/worm-style outbreaks where hosts become DDoS agents, this scenario focuses on segmentation, rapid endpoint containment, and eradication verification. It includes operational coordination steps to reduce collateral network impact.
Scenario 3: Stolen Documents
This scenario supports investigations where sensitive files are stolen or accessed without authorization. It emphasizes scoping access paths, validating data exposure, and coordinating Legal/Comms decisions for notifications and internal remediation.
Scenario 4: Domain Name System (DNS) Server Denial of Service (DoS)
DNS disruption can halt business operations quickly; this template drives triage, traffic analysis, failover decisions, and customer impact management. It also supports coordination with providers and communications planning for service status updates.
Scenario 5: Unknown Exfiltration
When you suspect data leaving your environment but lack full clarity, this scenario focuses on detection sources, scoping methodology, and containment without destroying evidence. It helps teams define what “proof of exfiltration” looks like for executive decisions.
Scenario 6: Unauthorized Access to Payroll Records
This scenario addresses sensitive employee data exposure, including HR and Legal coordination, privilege boundaries, and notification criteria. It reinforces careful evidence handling and internal communications to reduce employee trust impacts.
Scenario 7: Disappearing Host
A “missing” or wiped host can signal attacker cleanup or a failing asset process; this scenario drives discovery, logging validation, and asset/inventory integrity checks. It also supports decisions on reimaging, account rotation, and broader compromise assessment.
Scenario 8: Telecommuting Compromise
Built for remote worker incidents (home network, endpoint compromise, VPN abuse), this template prioritizes containment, credential hygiene, and secure re-onboarding of the user/device. It also covers practical communication steps for remote employees.
Scenario 9: Anonymous Threat
For extortion emails, anonymous tips, or threats of attack, this scenario provides triage criteria, credibility assessment, and escalation logic. It helps avoid overreaction while ensuring a defensible, documented response posture.
Scenario 10: Peer-to-Peer File Sharing
This scenario addresses policy violations and data leakage risks created by P2P tools. It includes steps for detection, containment, HR coordination, and proving removal while maintaining acceptable-use defensibility.
Scenario 11: Unknown Wireless Access Point
Rogue APs can undermine network security; this scenario supports discovery, physical verification, and containment actions. It also includes steps for identifying connected devices and validating access scope.
Scenario 12: Ransomware with Data Theft (Double Extortion)
This scenario structures decisions around encryption containment, leak-site pressure, restoration prioritization, and communications. It supports executive decision points about operations continuity, third-party support, and regulatory/notification readiness.
Scenario 13: Business Email Compromise (BEC) / Fraudulent Payment
BEC response needs speed: message tracing, mailbox rule review, banking coordination, and fraud containment. This scenario also includes internal controls and verification steps to prevent repeat fraud attempts.
Scenario 14: Cloud Storage Misconfiguration (Public Bucket/Container Exposure)
Public exposure incidents require rapid access-log scoping and shared responsibility clarity. This scenario guides containment (lockdown), verification (what was exposed, for how long), and remediation (policy-as-code, guardrails).
Scenario 15: Third-Party / Vendor Compromise (SaaS Provider / MSP Compromise)
Vendor incidents introduce contractual and notification complexity; this scenario provides coordination steps, evidence requests, and documentation workflows. It also supports structured stakeholder communications and risk assessment for downstream impact.
Scenario 16: Insider Data Theft
This scenario integrates HR + Legal privilege considerations while protecting evidence and enforcing acceptable-use policies. It supports careful scoping, access review, and containment without tipping off the subject prematurely.
Scenario 17: Credential Stuffing / Account Takeover
A template for identity-based attacks, focusing on detection signals, rate limiting, password reset workflows, and customer support coordination. It also supports fraud mitigation steps and consistent customer communications when applicable.
Scenario 18: Web Application Vulnerability Exploitation
This scenario is designed for exploitation events (including “zero-day style” uncertainty), balancing patch urgency with forensic needs. It includes compensating controls (WAF rules), validation steps, and safe deployment decisions.
Scenario 19: Compromised Privileged Identity / IAM Misconfiguration (Cloud Role Abuse)
Privileged identity incidents require fast access restriction and key/role rotation; this scenario guides containment and cloud logging evidence gathering. It also supports decision-making on blast radius and controlled restoration of access pathways.
Scenario 20: Cryptomining / Resource Hijacking (Cloud Spend Spike)
This scenario addresses abnormal resource usage and cost spikes, with steps for identifying compromised workloads, shutting down malicious compute, and strengthening guardrails. It includes billing/finops coordination and “return to safe” verification.
Scenario 21: Lost/Stolen Endpoint with Sensitive Data (Laptop/Mobile)
This scenario helps validate encryption status, execute remote wipe/lockout, and determine exposure risk. It also supports notification decision-making and secure replacement onboarding steps.
How to Use This Suite (Practical Implementation Path)
A common approach for enterprise adoption:
- Finalize governance in the CSIRMP (owners, roles, authority, escalation).
- Customize the CSIRP and the Management Procedure so operations and leadership share the same process.
- Operationalize response discipline using the checklists, meeting templates, and logs.
- Run tabletop exercises using the scenario templates (start with your highest-risk scenarios first).
- Track improvements after exercises/incidents using action tracking and post-incident updates.
If you’re building or upgrading an enterprise Cybersecurity Incident Response Plan, the Cyber Security Incident Response Plan Template Suite gives you a structured, comprehensive foundation: governance (CSIRMP), operational response (CSIRP + procedures), execution discipline (checklists + logs), and real-world readiness (21 scenario templates with completed examples).
USER RATING:
Cyber Security Incident Response Plan Templates and Playbooks for $1,197 is rated 4.9 out of 5 by 360 users.
